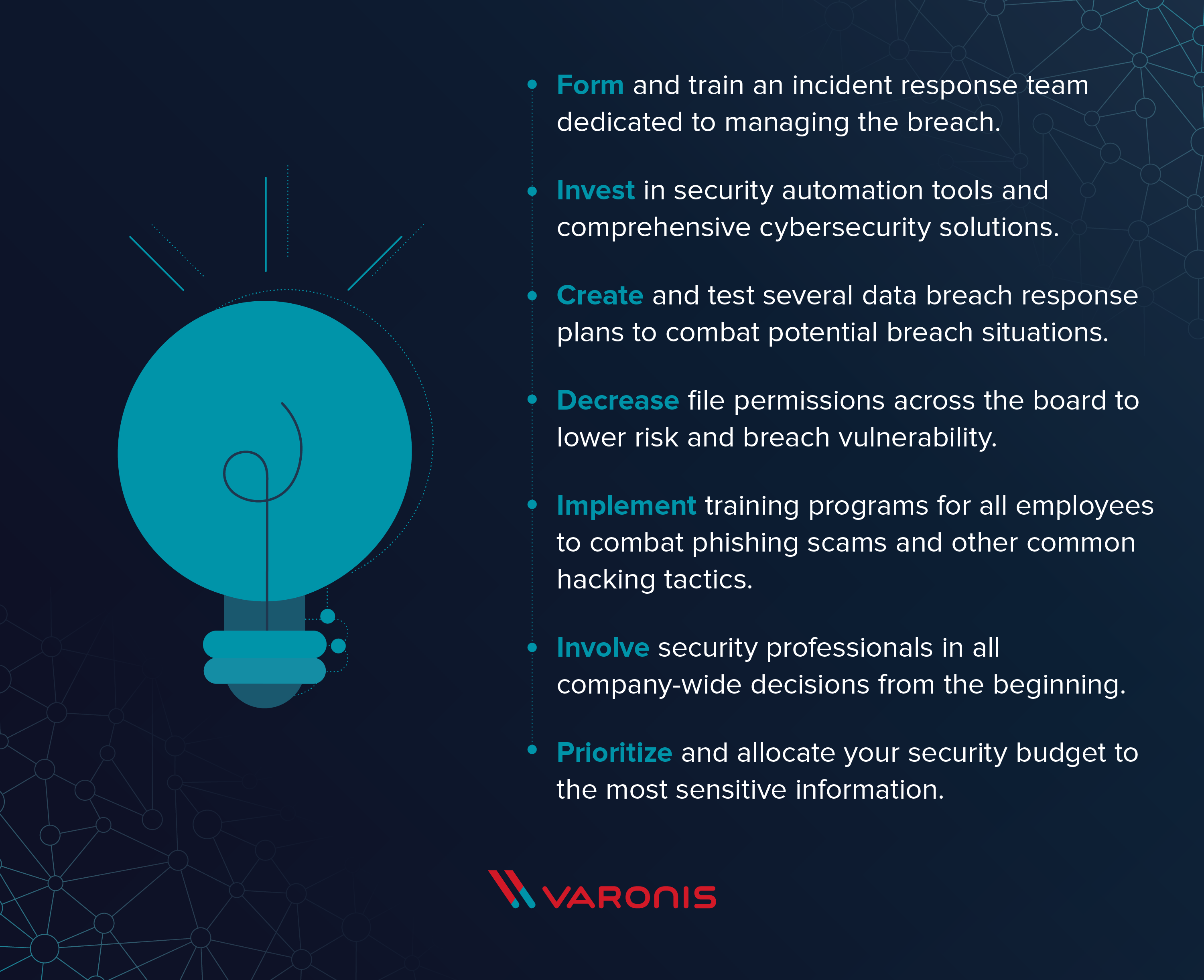
select the best answer. which of the following are breach prevention best practices
Business protection against cyberattacks and data breaches. Improved recovery time after a breach.

The Ultimate Data Breach Response Plan Securityscorecard
Which of the following are breach prevention best practices.
. The benefits of implementing and maintaining cybersecurity practices include. The deep hearty and distinctive flavor of rye has made it popular throughout history and it remains a staple in. The terms of the removal may prohibit the student from attending or participating in school-sponsored or school-related activity.
The Bakers Tables best-selling Bara Harvard loaf is a mix of Talgarth Mill rye flour and a strong white flour. Then select Check For Updates. In May 2019 the Data Breach Prevention and Compensation Act was passed.
All of the above answer. We recommend that you store this grain in a cool and dry place. All of this above answer Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents.
Protection for end users and endpoint devices. This means they are able to deliver high quality assignments. Yahoo also discovered a second major breach that occurred in 2014 affecting 500 million email accounts.
These countries may not have similar data protection laws and. 7 ash medium ryes ash content is in the neighborhood of 1. After all compliance is a top area of focus and concern for both human resources departments and company executives.
This writers are also assigned a. Before drawing up your list its a good idea to understand the nature of compliance and how it should be handled throughout the company. You have 0 of this in your trolley.
Following a full investigation into the 2013 data breach Yahoo disclosed that the incident affected all of the companys 3 billion email accounts. Protection for data and networks. Aug 02 2021 Windows 10 has the ability to mirror your screen to any dongle or device ex streaming box TV compatible with the popular.
The principal may not return the student to that teachers class without the teachers consent unless the committee established under Section 37003 determines that such placement is the best or only alternative available. For those instructors who wish to monitor students live during an test while still utilizing the LockDown Browser it is possible to have an active Zoom meeting during the quiz. This group of writers have passed strict English tests plus tests from their fields of specialization.
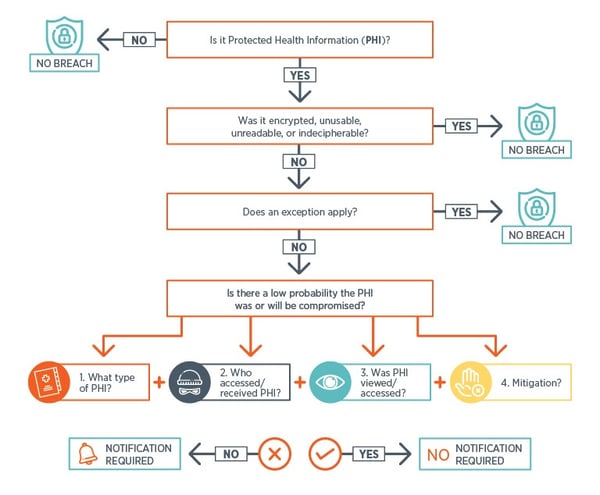
What of the following are categories for punishing violations of federal health care laws. Prevention of unauthorized user access. If you are based in the European Economic Area EEA or Switzerland we take all steps possible to ensure that your personal data remains within those areasHowever in some cases we need to share data with other YouGov group companies or third parties that are in countries outside those areas.
This means they recently joined the team. Best available This refers to a group of writers who are good at academic writing have great writing skills but are new in our team of writers. It created an Office of Cybersecurity at the.
Its in every businesss best interest to have an HR compliance checklist.
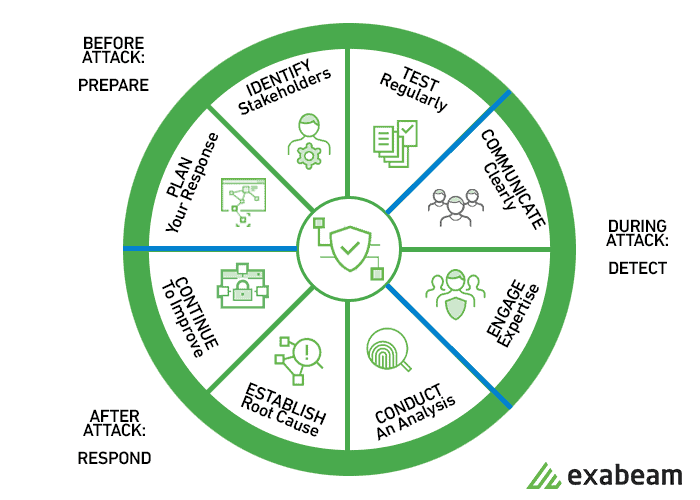
Incident Response Plan 101 How To Build One Templates And Examples
What Is A Data Breach Definition Types Dnsstuff

Handling Data Breaches In Your Business Privacy Policies

Mitigating Insider Threats Plan Your Actions In Advance Ekran System

7 Key Steps To Investigate A Data Breach With Checklist Ekran System

Case Study Comparison Hipaa Data Breaches And Phi On Stolen Laptops

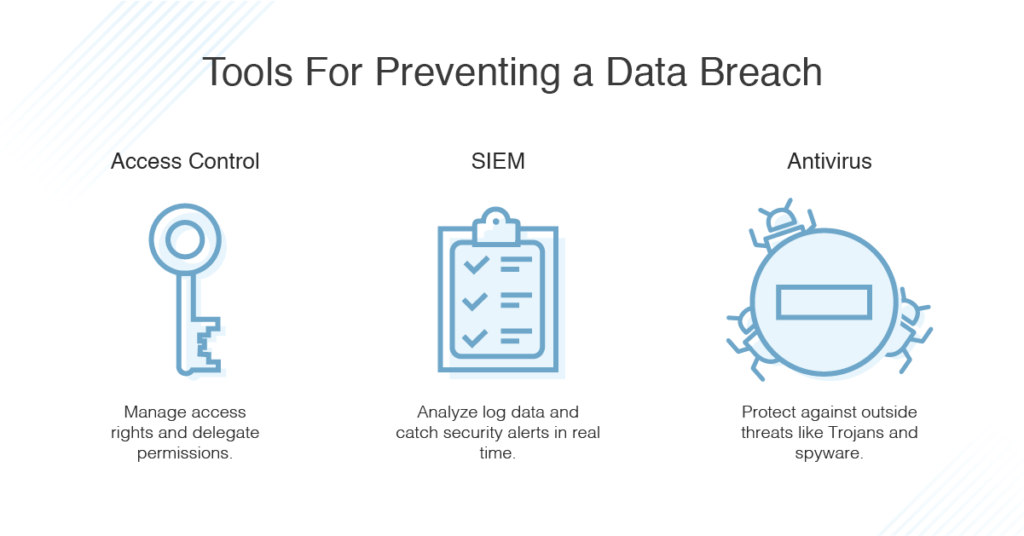
Data Loss Prevention Best Practices Endpoint Protector

7 Key Steps To Investigate A Data Breach With Checklist Ekran System